DNSSEC – Till vilket pris?
I senaste numret av Cisco IP Journal Volume 13 Number 1 så belyses ett problem som uppstår när DNSSEC börjar att användas och bandbreddsförbrukningen mer än dubbleras: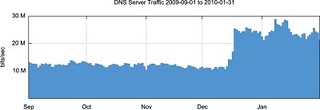
In other words, in this example scenario with stale Trust Anchor keys in a local client’s resolver, a single attempt to validate a single DNS response will cause the client to send a further 844 queries, and each .com Name Server to receive 56 DNSKEY RR queries and 4 DS RR queries…
The problem with key rollover and local management of trust keys appears to be found in around 1 in every 1,500 resolvers in the in-addr.arpa zones. With a current client population of some 1.5 million distinct resolver client addresses each day for these in-addr.arpa zones, there are some 1,000 resolvers who have lapsed into this repeated query mode following the most recent key rollover of December 2009. Each subzone of in-addr.arpa has six Name Server records, and all servers see this pathological re-query behavior following key rollover.



1 comments